For anyone embarking on a journey into the world of networking, the OSI (Open Systems Interconnection) Model is a foundational concept you’ll encounter early and often. Think of it as the blueprint or the language that helps different networking hardware and software communicate effectively. While you might not directly configure the “Presentation Layer” on a router, understanding the OSI model provides a crucial framework for troubleshooting, design, and overall comprehension of network operations. Let’s break down this 7-layer wonder, one step at a time!
What is the OSI Model?
The OSI model is a conceptual framework created by the International Organization for Standardization (ISO) in the 1970s. It standardizes the functions of a telecommunication or computing system into seven distinct layers. Each layer has a specific role and communicates with the layers above and below it. This layered approach simplifies the complexity of network communication.
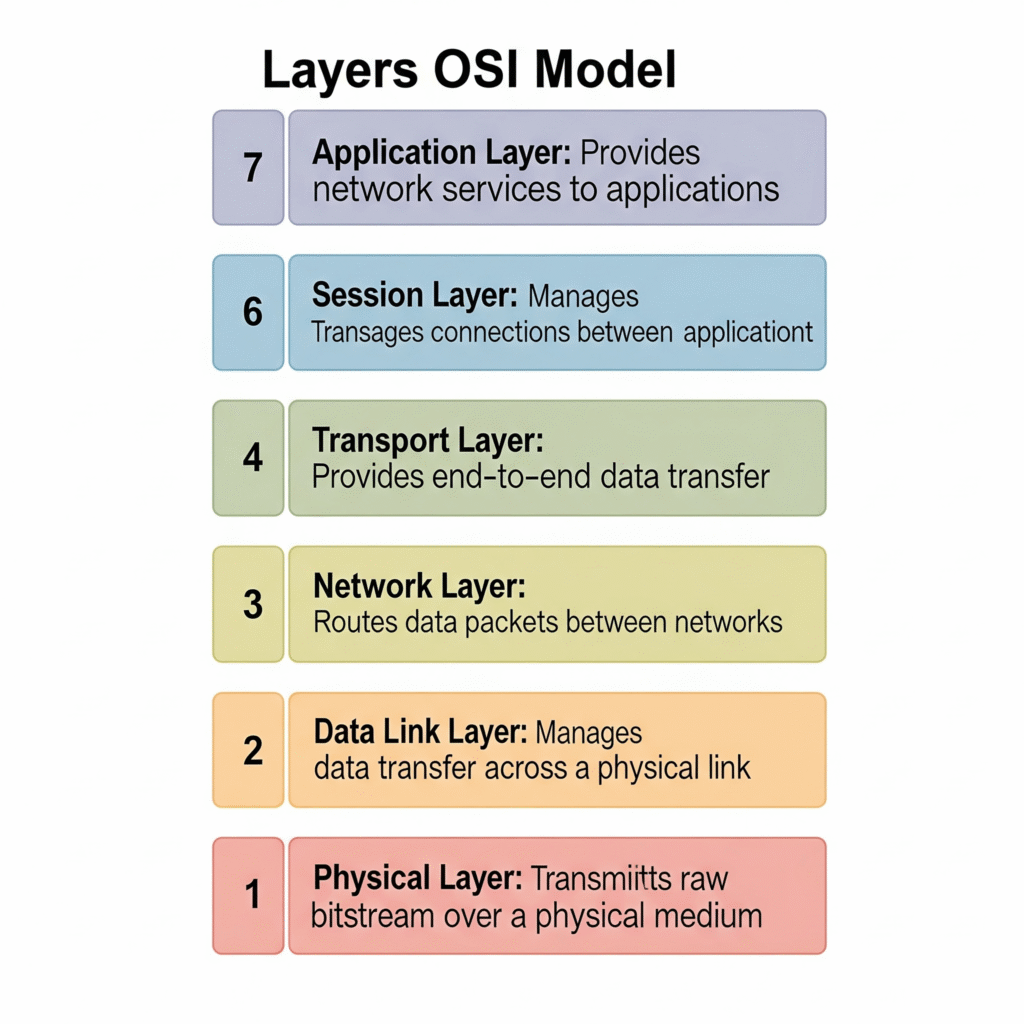
The 7 Layers of the OSI Model (Bottom-Up)
Think of the OSI model like a stack of pancakes, where each pancake (layer) has a specific job in the breakfast-making process.
- Physical Layer (Layer 1): The Foundation
- What it does: This layer deals with the physical connection and the transmission of raw data bits over a physical medium (like cables, fiber optics, or wireless). It defines the electrical, mechanical, procedural, and functional specifications for activating, maintaining, and deactivating the physical link.
- Think of it as: The actual Ethernet cable, the Wi-Fi radio waves, the connectors. It’s the tangible part of the network.
- Key technologies: Ethernet cables (Cat5e, Cat6), fiber optic cables, Wi-Fi (802.11 standards), Bluetooth.
- Data Link Layer (Layer 2): Addressing the Local Network
- What it does: This layer is responsible for reliable data transfer between two directly connected nodes over the physical layer. It handles physical addressing (MAC addresses), error detection, and flow control within the local network segment. It’s often divided into two sublayers: Media Access Control (MAC) and Logical Link Control (LLC).
- Think of it as: Ensuring that data gets from one specific computer to another within the same room or local network.
- Key technologies: Ethernet protocol, MAC addresses, switches, network interface cards (NICs).
- Network Layer (Layer 3): Routing Across Networks
- What it does: This layer is responsible for routing data packets from a source to a destination across multiple networks. It handles logical addressing (IP addresses) and determines the best path for data to travel.
- Think of it as: The postal service, figuring out the best route to send a letter across different cities or countries.
- Key technologies: IP (Internet Protocol), routers, IP addresses.
- Transport Layer (Layer 4): Reliable and Ordered Delivery
- What it does: This layer provides reliable (TCP) or unreliable (UDP) data delivery between applications. It handles segmentation of data, reassembly, error recovery, and flow control on an end-to-end basis.
- Think of it as: Ensuring that all the pages of a book you ordered arrive and are in the correct order.
- Key technologies: TCP (Transmission Control Protocol), UDP (User Datagram Protocol), port numbers.
- Session Layer (Layer 5): Managing Connections
- What it does: This layer establishes, manages, and terminates connections (sessions) between applications. It handles authentication and authorization.
- Think of it as: Starting, managing, and ending a phone call or a video conference.
- Key technologies: NetBIOS, SIP.
- Presentation Layer (Layer 6): Data Formatting and Encryption
- What it does: This layer is responsible for data formatting, encryption, and compression. It ensures that data sent by the application layer of one system is readable by the application layer of another system.
- Think of it as: Translating a document from one language to another or zipping a file to make it smaller.
- Key technologies: ASCII, JPEG, MPEG, SSL/TLS encryption.
- Application Layer (Layer 7): The User Interface
- What it does: This is the layer closest to the end-user. It provides the interface for network applications to access network services.
- Think of it as: The web browser you use to access websites, the email client you use to send emails, or the file transfer protocol (FTP) client you use to download files.
- Key technologies: HTTP, HTTPS, SMTP, POP3, DNS, FTP.
Why is the OSI Model Important?
- Conceptual Framework: Provides a common language and reference point for discussing network functionality.
- Troubleshooting: Helps to isolate problems to a specific layer, making troubleshooting more efficient.
- Understanding Technologies: Explains how different networking technologies and protocols work together.
- Learning Foundation: It’s a fundamental concept taught in networking certifications like CompTIA Network+ and Cisco CCNA.
Conclusion
The OSI model provides a structured way to understand the complex processes involved in network communication. By grasping the role of each layer, aspiring network engineers gain a solid foundation for further exploration into the fascinating world of networking technologies and protocols. Keep this “stack of pancakes” in mind as you continue your learning journey!
