Why Some USB Cables Can Be Dangerous – And How to Stay Safe
Most of us think of USB cables as simple tools: you plug one in to charge your phone, connect a device, or transfer files. But what if I told you that some USB cables aren’t just cables—they’re potential threats?
In recent years, security researchers (and unfortunately, cybercriminals) have demonstrated that malicious USB cables can hide tiny computer chips inside. These chips allow the cable to do much more than pass electricity or data. In fact, they can be weaponized to deliver harmful payloads.
Let’s break down why this is a risk, and how you can protect yourself.
How a Malicious USB Cable Works
At first glance, a “bad” USB cable looks identical to a normal one. The difference is what’s inside. Security experts have built proof-of-concept cables, such as the “O.MG Cable”, that contain hidden electronics capable of:
- Keylogging – Capturing everything you type if connected to a keyboard.
- Payload Injection – Running malicious scripts or commands on your computer as soon as it’s plugged in.
- Remote Access – Allowing attackers to control your system over Wi-Fi, without you even realizing it.
- Data Theft – Extracting sensitive files when the cable is connected to your PC or phone.
These cables are often indistinguishable from the real thing—you wouldn’t know one was dangerous just by looking at it.
Why This Matters
Most people are cautious about clicking suspicious links or downloading unknown files. But when it comes to hardware, we tend to trust the physical things we plug into our devices. That trust can be exploited.
Imagine borrowing a USB charging cable at an airport or hotel. It might not just charge your phone—it could secretly attempt to compromise it. Likewise, a malicious cable handed out at a conference or “gifted” by someone could be a Trojan horse.
How to Stay Safe
Fortunately, there are practical steps you can take to protect yourself:
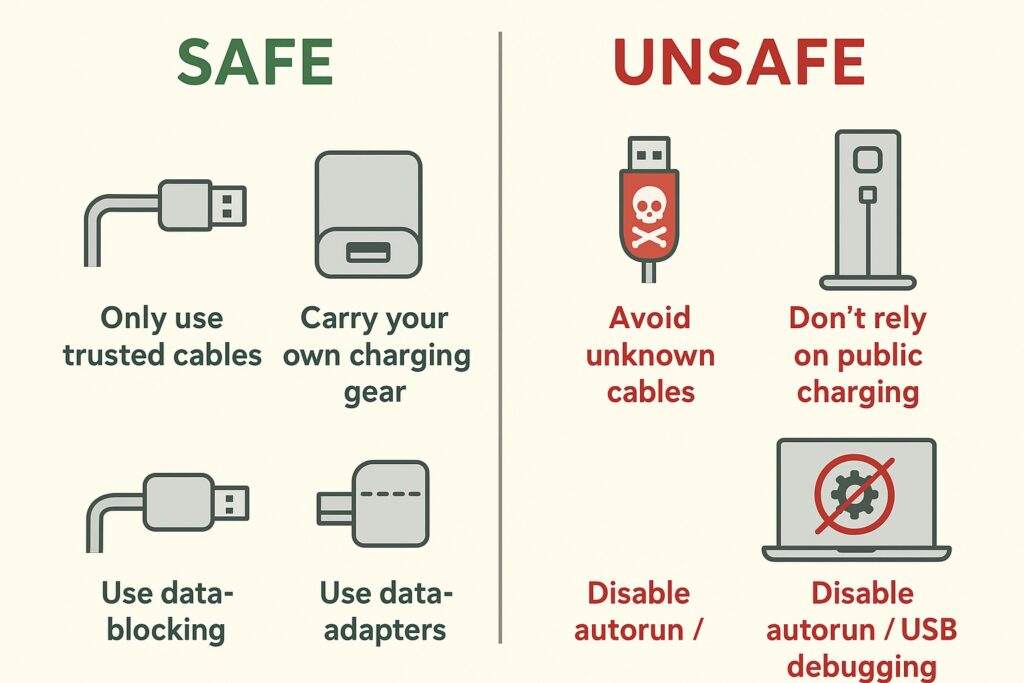
1. Only Use Trusted Cables
Stick to cables from reputable brands and sources. Avoid “freebies” or unbranded cables of unknown origin.
2. Carry Your Own Charging Gear
When traveling, bring your own USB cable and charger. Don’t rely on public charging stations where you don’t control the hardware.
3. Use Data-Blocking Adapters
Also called “USB condoms,” these adapters allow only power to pass through while blocking data connections. Great for public charging situations.
4. Disable Autorun / USB Debugging
On laptops and mobile devices, disable features that automatically trust connected devices. This reduces the chance of an injected payload running silently.
5. Stay Informed
Cyber threats evolve constantly. Knowing that malicious hardware exists helps you make safer choices.
Final Thoughts
USB cables are so common that it’s easy to forget they can be more than just plastic and wires. Malicious cables represent a new frontier in cyberattacks—blending the physical and digital worlds. By practicing caution and sticking to trusted equipment, you can dramatically reduce your risk.
Your cable should charge your device, not compromise it. Stay safe, stay aware, and don’t underestimate the threats hiding in everyday tech.
